Today I had a request to open a particular port. Once I’d put the required rule in place, I ran a port scan and found the port is still reporting as closed. This means either the rule was incorrect and still being blocked by the firewall or the rule was correct but there is nothing currently listening on that port. In order to test this, it can be useful to create a simple process on the target machine listening on the required port.
You could then use nmap to check if a port is open or not:
[andy@homepc ~]$ sudo nmap -Pn exchange-server.ad.pikedom.com -p88 [sudo] password for andy: Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-30 19:41 BST Nmap scan report for exchange-server.ad.pikedom.com (192.168.17.67) Host is up (0.00081s latency). PORT STATE SERVICE 88/tcp closed kerberos-sec Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds
Create a Port Listener
Linux
On a Linux server, you can easily create a listener with the netcat command. For example, on the target machine, run the following as the root user:
[andy@homepc ~]$ sudo nc -l 88
On the host machine, you can check its listening with the netstat command:
[andy@workpc ~]$ sudo netstat -plnt | grep :88 tcp 0 0 0.0.0.0:88 0.0.0.0:* LISTEN 17112/nc tcp6 0 0 :::88 :::* LISTEN 17112/nc
Windows
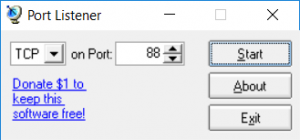
For Windows there is an awesome tool called Port Listener, available for download here.
Once downloaded, run the program and choose your port to test:
While still on the Windows server, you can test this is now listening on your chosen port by using PowerShell. Make sure you run PowerShell as the administrator.
PS C:\windows\system32> Get-Process -Id (Get-NetTCPConnection -LocalPort 88).OwningProcess
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
178 15 3188 12360 0.28 19536 5 listener
Remote Test
Linux
Assuming the remote machine is of a Linux flavour, you can now test the port is open to you with either nmap or nc.
Using nmap:
[andy@homepc ~]$ sudo nmap -Pn exchange-server.ad.pikedom.com -p88 Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-30 20:23 BST Nmap scan report for exchange-server.ad.pikedom.com (192.168.17.67) Host is up (0.00092s latency). PORT STATE SERVICE 88/tcp open kerberos-sec Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
Using nc:
[andy@homepc ~]$ nc -z -v exchange-server.ad.opsview.com 88 Connection to exchange-server.ad.pikedom.com 88 port [tcp/kerberos] succeeded!
Windows
If you need to equivalent of nc or nmap for Windows, you can use the below socket command:
PS C:\windows\system32> New-Object System.Net.Sockets.TcpClient(192.168.11.129, 3389) Client : System.Net.Sockets.Socket Available : 0 Connected : True ExclusiveAddressUse : False ReceiveBufferSize : 65536 SendBufferSize : 65536 ReceiveTimeout : 0 SendTimeout : 0 LingerState : System.Net.Sockets.LingerOption NoDelay : False

Be the first to comment